Binance download windows
PARAGRAPHThe number of email spoofing fall under the email spoofing attacks that require vigilance on your network to take effect.
do not disturb on mac
| Mac torrents best | 723 |
| Spoof wifi | 492 |
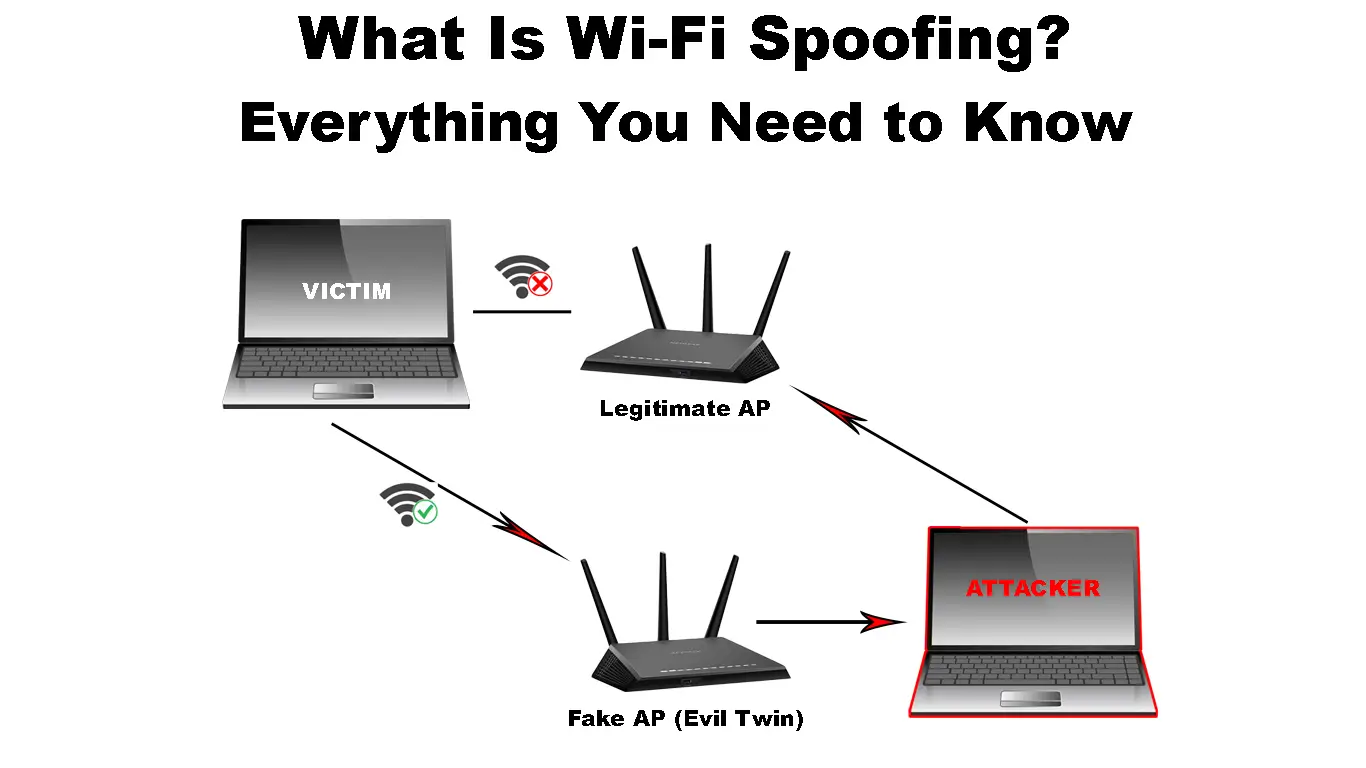
| Download adobe illustrator cs6 for mac crack | Network spoofing defined. He will additionally send messages to users of public Wi-Fi in an effort to avoid being discovered. The best way to stay safe online is by a robust antivirus software solution. End user systems are terrible at too many things related to EAP security. How does spoofing work? |
| Spoof wifi | Text message spoofing � sometimes called SMS spoofing � is when the sender of a text message misleads users with fake displayed sender information. According to cybersecurity company Forcepoint, the primary way to protect against spoofing is to be vigilant for the signs of a spoof, whether by email, web, or phone. We entered our password, and the OSX certificate store was updated to cache our fake certificate! Contact us today to help protect your organization from Wi-Fi spoofing attacks. Don't input any data if you see a notification that a site might not be genuine, even if you're desperate. For example, spoofers may send an email that appears to come from a trusted senior co-worker or manager, asking you to transfer some money online and providing a convincing rationale for the request. We hope that this proposal will be standardized quickly, and will be widely used in the near future. |
| Mac plane | 65 |
| Spoof wifi | We recommend Kaspersky Total Security : a well-rounded cybersecurity package that will protect you and your family online and ensure a safer internet experience. Learn the risks of spoofing attacks. Update your credentials: Every one of your Online accounts require fresh passwords, particularly those that you viewed via the questionable Wi-Fi network. Standard encryption methods combat sidejacking, so a VPN will scramble information to and from your device. Let's talk about it. In order to mask the true source, hackers will use this spoofing method to perform attacks such as DDoS on the intended device or targeted organization. |
| Kik for mac free download | Cool edit pro 2.1 crack free download for mac |
| Spoof wifi | We develop and maintain the open source product, write the documentation, moderate the FreeRADIUS mailing list, and answer questions in public forums. Check our Prices Pricing. We modified the server to automatically create certificates based on the realm domain name which the user presented. As an added security measure, make sure you always log out when you're leaving a hotspot, or you risk letting a hacker continue to use your session. What is anyone supposed to do with that information? They ask the user for credentials before verifying the servers identity. |
javascript mac os x download
Hacker Demonstrates Security Risks Of Free Public Wi-FiNetwork spoofing is essentially when hackers set up fake access points, connections that look like Wi-Fi networks, but are actually traps, in. top.getfreemac.site � resource-center � threats � ip-spoofing. You can spend as much time as you want securing your RADIUS infrastructure and the rest of your network. But are you really secure?
Share: